Cybersecurity is one the biggest fears of engineers and industrial companies as we enter the interconnected age. The Internet of Things (IoT) is connecting several of our new devices to online networks and cloud computing, as well as retrofitting our legacy systems. Placing these systems on accessible networks opens the door for cyberattacks. This past month, cyber activity from the Russian government targeted U.S. power plants along with other infrastructure facilities. As we place our systems online, what can be done about protecting our infrastructure from cyberattacks?
Government and IoT
In 2016, the Center for Data Innovation conducted research into how IoT devices are being used by the government. Some of the areas that the government is using IoT is in smart buildings, vehicle fleet monitoring, asset monitoring, and agriculture. As result of increased use of IoT devices, Congress passed the Internet of Things Cybersecurity Improvement Act of 2017 to help secure future IoT devices and their data.
Within our energy infrastructure, the Office of Electricity Delivery and Energy Reliability’s (OE) mission statement is to “pursue technologies to improve grid reliability, efficiency, flexibility, functionality, and security; and making investments and sponsoring demonstrations aimed at bringing new and innovative technologies to maturity and helping them transition to market.” The four critical challenges that need to be addressed per the OE are as follows:
- Changes in demand driven by population growth, adoption of more energy efficient technologies, dynamic economic conditions, and broader electrification, including possible mass-markets for electric vehicles.
- Changes in the supply mix (such as renewables, nuclear energy, natural gas, and coal) and location (centralized, distributed, and offshore) of the Nation’s generation portfolio driven by technology, market, and policy developments.
- Increasing variability and uncertainty from both supply and demand, including integration of variable renewables, more active consumer participation, and accommodating new technologies and techniques.
- Increasing challenges to the reliability and security of the electric infrastructure (such as more frequent and intense extreme weather events, cyber and physical attacks, and interdependencies with natural gas and water).
Several of these challenges will be addressed by introducing new technology, and these devices will be IoT-enabled devices, connecting them to the internet and other energy networks.
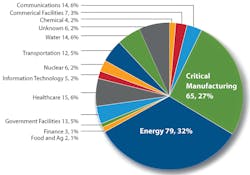
In 2014, Industrial Control Systems Cyber Emergency Response Team received and responded to 245 incidents reported by asset owners and industry partners. The Energy Sector led with the most reported incidents, which according to the Statista Research firm had an average financial cost of $26.5 million. (Image Credit: ICS-CERT)
Cyberattacks on U.S. Energy
Our current energy infrastructure is already under attack from cyber threats. This month, as mentioned above, the U.S. Computer Emergency Readiness Team reported that Russian cyberattacks targeted our government and domestic sectors in energy, nuclear, commercial facilities, water, aviation, and critical manufacturing sectors.
These attacks are part of an ongoing trend. According to a report from The Hill, the Department of Energy was hacked 159 times between 2010 and 2014. Records obtain by The Hill under the Freedom of Information Act revealed that hackers targeted DoE networks 1,131 times over the four-year span.
The problem is only increasing as we expand our energy networks. A 2016 MIT study found that due to grid expansion and the growing demand on our energy infrastructure, “system operators must have the capacity to operate, maintain, and recover a system that will never be fully protected from cyberattacks.”
A recent Forbes article highlighted the many exposed access points in our energy networks. According to the article, a study from the U.S. National Institute of Standards and Technology Cybersecurity Working Group identified 137 types of vulnerable access points between different grid systems: “For example, every smart meter and most sensors and major pieces of equipment at generating plants and substations will have communications modules, using millions of components from potentially hundreds of manufacturers. Software applications will also be provided by many different developers.”
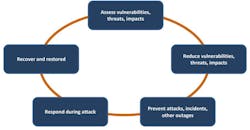
According to the MIT study on cybersecurity, vulnerabilities need to be assessed and reduced to prevent cyberattacks whenever possible. When attacks do occur, an effective, speedy response and a well-thought-out plan for recovering and restoring operations are needed, as highlighted in the Cybersecurity Life Cycle above. (Image Credit: MIT)
Approaches to Cybersecurity
Currently there is no one organization in place to oversee cybersecurity for electric grid systems. The OE and The North American Electric Reliability Corporation have developed standards on how to properly protect these systems, but the responsibility for implementation is left to the industrial companies.
Holistic industrial security is an effort that involves the entire plant and encompasses every device. It should address risk from people, unsecure processes, and vulnerable technologies. According to the MIT study, here are some important points to consider when developing a security plan:
- Industry needs to adopt cybersecurity best practices and develop a risk management culture; cybersecurity regulations are important, but because there is a delay in developing and implementing them, regulations lag behind evolving threats.
- It is important to rapidly share information about cyber threats while respecting privacy guidelines.
- Good cybersecurity requires skilled teams to understand baseline operations, detect and respond to anomalous cyber activity, reduce the “dwell time” of cyber attackers, and implement layered cyber defenses.
- The is a need to understand and increase system resilience to avoid prolonged outages and better recover from cyber attacks.
- In the future, utilize advanced cybersecurity technologies, international approaches to cybersecurity, and machine-to-machine information sharing so the response to cyber incidents takes place in milliseconds—not months.
A recent article from Rockwell Automation listed its approach to power plant cybersecurity in three steps:
Security Assessment
Cultivate a deep understanding of all risks and vulnerabilities that exist within your organization. A security assessment offers thorough review of site infrastructure nuances, software, networks, control systems, policies, procedures, and even employee behaviors. It’s the foundation for a successful security policy.
A proper security assessment should include:
- Inventory of authorized and unauthorized devices and software.
- Detailed observation and documentation of system performance.
- Identification of tolerance thresholds and risk/vulnerability indications.
- Prioritization of each vulnerability based on impact and exploitation potential.
- Mitigation techniques required to bring an operation to an acceptable risk state.
Defense-in-Depth Security
Defense-in-depth (DiD) security is the idea that if any one point of protection is defeated, there are additional layers to protect the system that will need to be defeated for a hacking attempt to be successful. DiD security approaches establish multiple layers of protection through a combination of physical, electronic, and procedural safeguards. A DiD security approach consists of six main components:
- Policies and procedures
- Physical
- Network
- Computer
- Application
- Device
Trusted Vendors
Selecting vendor partners that have the appropriate level of security can have a large impact on helping you meet your security goals. Before selecting vendors for any system that will be connected to your network, request that they disclose their security policies and practices. Rockwell Automation, through its partnership with Cisco, has defined five core security principles for designing products used in a control system:
- Secure network infrastructure
- Authentication and policy management
- Content protection
- Tamper detection
- Robustness
Power plants that run our energy networks should look for a structured and tailored approach to meet physical and cybersecurity requirements. As the world of IoT continues to grow, companies will have to adopt multiple layers of protection and backup systems to ensure a secure energy system that can function without interruptions.