The Industrial Internet of Things (IIoT) is changing the way business owners view their factories by giving them real-time data from machines and devices in the field that let them monitor and control production. Overall equipment effectiveness (OEE) and zero equipment downtime are no longer just buzzwords; they are critical for manufacturing business is to succeed.
This new trend is compelling machine builders to provide IIoT tools that support zero downtime and high OEE. Remote access technology helps machine builders achieve these goals.
Data collected from experienced support engineers indicate that an estimated 60% to 70% of machine problems simply require a software upgrade or changes to a few parameters, and these can often be done remotely. Remote access lets machine builders avoid time-consuming and expensive on-site work for troubleshooting many problems in the field.
Furthermore, with remote access, machine builders acquire real-time data from their installed machines. And, based on actual equipment conditions, machine builders can accurately predict machine failures. This lets managers schedule maintenance services in advance, thus improving their machines’ availability, in addition to improving product quality and speed.
A remote desktop connection (RDC) network.
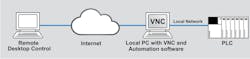
Some machine builders rely on traditional remote-access such as virtual private networking (VPN) and remote desktop connection (RDC), which uses virtual network computing (VNC). Both improve service and let builders respond quicker to customers. However, the limits on traditional remote access hold back machine builders from providing better service.
A virtual private networking (VPN) setup.
Challenges in Using VPN and RDC
VPN and RDC can simplify the task of setting up secure connections to remote machines. However, they lack the flexibility or intelligence to meet machine builders’ specific needs. The five key elements machine builders must consider when using VPN and RDC are:
- Time-consuming setup requires extensive IT knowledge. Several parameters—including IP address, domain name, key ID, authentication mode, a suitable encryption algorithm, and an efficient hash function—must be configured to properly establish connectivity with remote machines and exchange necessary authentication keys and data. This process is complex, time consuming, and requires extensive IT knowledge, which most automation engineers are not familiar with.
- Compromises in corporate security policies are needed for remote access to machines. VPNs need a server with a static public IP address, and some specific network ports must be configured to permit inbound and outbound traffic. In the inbound firewall rules, users must create NAT rules and let port forwarding allow inbound VPN connections. In the outbound firewall, UDP port 500 or 4500, or some other designated port, needs to be configured to handle outbound VPN connections. Most IT departments are unwilling to implement such changes in their organization’s network because it may create network vulnerabilities and compromise network security. Creating secure and flexible firewall rules has proven a major challenge for most IT departments, especially those managing industrial networks.
- Securing remote connections involves complexity and high cost. VPN connections between machine builders and machine operators are usually site-to-site connections that typically give the builders remote access to all local devices in a plant’s network. Plant operators want to restrict machine builders’ access so only certain machines are accessible. For example, plant operators need ways to limit access by plant equipment and specify applications that can be accessed remotely to prevent unauthorized access to production information and unauthorized or accidental operation of plant equipment. The only way to mitigate this risk is for IT departments to create separate end-to-end connections using VPNs, which (as previously noted) is complex and expensive, thereby drastically increasing setup and maintenance costs.
RDC connections are equally troublesome in that they expose plant-network computers to the public network, creating security risks. Computers need regular security-patch updates, which are carried out when they connect to public networks such as the plant’s Wi-Fi. But plant computers are then vulnerable during the access windows to the public network (if they are also open to RDC control). They can become targets of network attacks and be susceptible to ransomware injections. Mitigating these security issues requires additional resources, both in terms of staff resources and maintenance.
- VPN security is hard to manage. One way to achieve a higher level of security is to have different pre-shared keys or X.509 certificates for each VPN tunnel. When the number of VPN tunnels/connections required are few, it is easy to manage the keys or certificates for these connections. However, as the number of VPN tunnels grows, it becomes very hard to manage these keys and certificates. When VPN servers or client systems are changed, certificates must be regenerated. When a certificate expires, a new certificate must be assigned and reloaded, which further complicates maintenance.
- VPN and RDC scalability and flexibility bring extra costs. VPN servers are typically limited in the number of VPN tunnels they support. When a business grows, more and more machines and devices connect to the network with an increasing number of engineers supporting business operations. This leads to an increase in VPN connections required. Once this number exceeds the VPN server’s capabilities, machine builders need to install a new VPN server and go through another time-consuming configuration process.
VPN servers are typically housed in the machine builder’s centralized service center. Many VPN clients in remote sites connect to VPN servers in the center. Support engineers typically do not have access to the server when outside the center. To access those servers from outside the center (by OpenVPN or L2TP over IPsec, for example), they must be installed at remote sites, and each needs a public IP address. This results in high installation and maintenance costs. In addition, remote connections require different network subnets on the server side and the client side. If engineers want to simultaneously diagnose remote equipment on different sites, they must be aware of the IP subnet configurations at the remote IP sites to prevent IP address conflicts and other problems.
Similarly, a remote desktop connection to a PLC/controller is neither straightforward nor convenient. It requires, at a minimum, a dedicated PC with all the relevant software tools installed and connected to the machine. As a business grows, the number of dedicated PCs and software-tool licenses increases, leading to a steep rise in IT costs. In addition, managers need to consider PC maintenance and the software tools installed on them. Machine builders prefer identical versions of the software tools be installed on both client and host machines because this simplifies troubleshooting. To do so, IT engineers assigned to maintenance need to coordinate updates to software tools between the server and client sides.
Because of these limitations and restrictions in VPN- and RDC-based remote access, machine builders and equipment manufacturers want an easy-to-use, secure, flexible, and scalable approach they can use to remotely manage machines and equipment.
Cloud-Based Secure Access
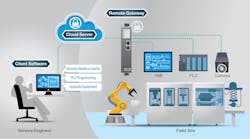
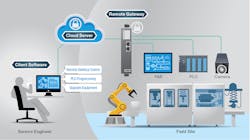
Cloud-based access is a new type of secure, remote access that would allow flexible remote access to field machines. Its network topology consists of three components: a remote gateway, a cloud server, and client software. Remote gateways connect to field equipment to access and control them. Client software gets installed on the engineer’s PC or desktop. The remote gateway and client software initiate outbound secure connection requests to the cloud server.
Promo and Graphic: G4 Promo and graphic
A cloud-based secure remote access network.
The cloud server is installed on a cloud-based platform such as Amazon Web Services or Microsoft Azure. It maps the connection requests and, after successful authentication on both sides, establishes a connection.
Cloud-based access implements network topology that enables the creation of outbound connections in the form of remote access tunnels, thereby effectively overcoming the challenges presented by traditional VPN and remote desktop control technologies. In addition, cloud remote access based brings machine builders the following benefits:
Ease of Use
a) Plug and play remote access does not need technical configuration. Security parameters, such as hash functions and encryption/decryption algorithms, are configured automatically. Machine builders do not need to configure these parameters; they just need to click on a button to establish a remote connection.
b) Virtual IP addresses make multi-point access effortless, with no field IP reconfiguration needed. Irrespective of the initial IP addresses set up by machine builders, cloud-based software assigns unique virtual IP addresses to machines. Machine builders can use these virtual IP addresses to establish several simultaneous remote connections. In addition, machine builders can use identical IP schemes for different field sites without worrying about address conflicts, which cuts installation costs substantially.
c) The connection is centrally monitored and managed. The cloud server is the central point for establishing and managing remote connections. Administrators can monitor traffic status and volume of each connection by connecting to the cloud server. Furthermore, administrators can easily manage client accounts, remote gateways, and certificates without having to reconfigure frequently. Cloud-based server portals let administrators:
- Create, cancel, or redefine client access.
- Add or remove remote gateways and connected equipment through the centralized portal.
- Have the server act as the centralized certificate manager to automatically assign X.509 certificates to remotely access connection sand suspends connections until the certificates are verified.
Enhanced Security
a) End-to-end encryption between a remote PC and a piece of equipment prevents data leaks. The cloud server only routes traffic; it does not decrypt or store data that passes through.
b) Machine builders use remote access for troubleshooting, monitoring, maintenance, and diagnostics. Remote access is typically not required on a continuous basis and can therefore be used on an as-needed basis to minimize security issues and reduce costs, especially when remote connectivity is based on a volume-dependent pricing option, such as with cellular technology. Furthermore, machine operators want to prevent machine builders from remotely accessing all applications on their local network by limiting access to only the applications machine builders need, thereby eliminating the risk of interfering with plant operations. Cloud-based access lets machine operators initiate or accept remote connections. Furthermore, machine operators can establish rules as to which services and applications, such as HTTPS or Telnet, machine builders can remotely use. They can also restrict access to specific sets of service engineers.
c) IT security policies are followed with no compromises. Cloud-based access builds outbound connections using the outbound service port 443 (normally reserved for secure website access using SSL) to access remote equipment, which does not present any issues for IT departments managing plant networks. The access can work with the IT security policies of machine operators.
Flexibility and Scalability
a) Client software isn’t limited to specific hardware platform. Users can download client software to any laptop/PC and have remote access from anywhere and at any time, as long as they have an active client account.
b) Remote access to equipment lets users act as if they are locally connected.
A transparent tunnel connects the client with the remote equipment as if they were on the same network. So regardless of the remote equipment being accessed (e.g., a Siemens PLC or a Rockwell controller), and independent of the protocol used to pull data or for programming (such as an L2 broadcast packet or an L3 IP packet), machine builders can remotely acquire data or program remote equipment using their own software tools as if they were sitting next to the equipment.
c) It simplifies network expansion by letting network administrators easily add and remove equipment and manage client accounts and certificates.
OEMs and machine builders require secure, easy-to-use, on-demand and scalable remote access to their machines in the field. Traditional VPN and RDC access are cumbersome and require IT/networking knowledge, as well as changes in security/firewall policies. Remote access backed by a cloud-based management infrastructure can provide the ease-of-use, flexibility, and scalability required by OEMs, without compromising on security.
This was written by Blanch Huang, product manager at Moxa Inc. If you have any questions regarding IIoT and security or Moxa Remote Connect (MRC), please feel free to call the company at 888-669-2872 or e-mail usa@moxa.com