Digital Supply Chain: Cybersecurity Report Flags Clear and Present Danger
At a Glance:
- Throughout the pandemic, cyber perpetrators exploited vulnerabilities created by rapid digitization.
- A Netscout Threat Intelligence Report that focused on the second half of 2021 reported a 606% increase in attacks against software publishers, 162% increase in attacks on computer manufacturers and a 263% increase against computer storage manufacturing.
- An analysis showed that attackers are centering their efforts on the digital supply chain.
If the data in a newly released cybersecurity report holds sway, it means that cyber extortion attackers are innovating by devising new techniques to block technologies that allow users to get on the internet. What’s especially troubling is that they adapting those techniques to go after a specific group of manufacturers.
A Threat Intelligence Report prepared by Netscout, a cybersecurity, service assurance and business analytics solution provider, showed that during the second half of 2021, the digital supply chain experienced an upsurge in distributed denial-of-service (DDoS) attacks.
Those associated with software publishers and computer manufacturers are increasingly vulnerable. According to the bi-annual report, cybercriminals launched 606% more attacks against software publishers, 162% more attacks against computer manufacturers and 263% more attacks against computer storage manufacturers.
DDoS attacks refer to malicious breaks in normal traffic of a server or distributed network. The attackers exploit the target’s infrastructure (e.g., computer systems and other IoT devices such as smartphones, headphones and cameras). Unlike ransomware attacks, a DDoS ransom attack does not encrypt a company’s systems; they aim instead to knock users offline.
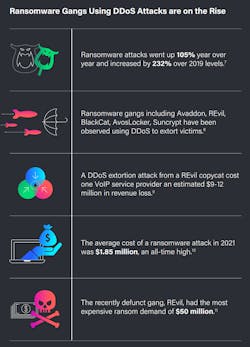
DDoS attacks are saturating the internet. According to the report, the 9.7 million attacks levied in 2021 is a 14% increase over the number of attacks that occurred in 2019 and represents a DDoS attack every three seconds.
Richard Hummel, a threat research lead at Netscout and lead author of the report, pointed out there’s a strong likelihood that enterprises have already had latency issues or experienced periods when the internet went offline due to DDoS attacks. “If you use the internet, you are absolutely impacted by DDoS attacks,” Hummel said.
Adversaries are going after VPN or DNS servers or internet exchanges—the networks that allow us to communicate. “They are going after this fundamental layer of what allows us to get on the internet and are specifically going after these manufacturers,” he said.
Telecommunications verticals tend to be a popular target for attacks, but saw fewer attacks in the latter part of 2021, reported Netscout. However, a notable exception occurred in the wireless telecommunications space, “where a likely increase in wireless hotspot gaming and the rapid adoption of 5G fueled increased attacks.”
Many companies went through rapid digitisation during the pandemic months. This reality sharply increased their attack surfaces if their IT was not sufficiently secured against attacks, explained Hummel.
Work-from-home didn’t help either. A spike in DDoS attacks coincided with the period during which people started working from home and when schools closed, and it persisted until about September of 2021, when “the world started returning to normal.”
The intimation, according to Hummel, is that remote work forced people to adapt their lifestyles and engage in recreational activities, such as gaming. “One thing that a lot of people don’t realize about the DDoS world is that 80% to 90% of all DDoS attacks are related to gaming of some sort—related either to individual gamers, gambling associated with that gaming and professional gaming,” he said. “Adversaries will launch attacks to knock their opponents offline.”
Disruptive Maneuvers
To understand the ramifications of a DDoS extortion attempt, look no further than the attack launched by a group known as Lazarus Bear Armada (LBA). The perpetrators unleashed an extortion attack on the New Zealand Stock Exchange in August 2020. “They stock market was offline for several days, and the service provider was having issues,” said Hummel. “LBA found a weak link and the target organization (NZX) was not entirely prepared to handle some of the attacks that were coming in.
“They weren’t necessarily novel attacks or new vectors that had never been seen before,” he continued. “It wasn’t super-high volumes. It was that the provisions were not in place to be able to handle some of these attacks.”
The attackers’ persistence at finding a weakness in an enterprise’s network is at the root of many DDoS attacks. In general, cybercriminals send their targets an email warning of the imminent attack unless a ransom is paid in cryptocurrency. If the demands are not met, the attackers repeatedly crash company websites or IT infrastructure by overwhelming them with volumes of online traffic. DDoS attacks succeed precisely because enterprises do not make provision for all the potential attacks or because they don’t have enough bandwidth to handle the influx.
“The LBA gang capitalized on that [weakness] and kept hammering and hammering and hammering and resulting in four days of downtime,” said Hummel. “And that cost a lot of money—a lot of revenue loss, the stock market was impacted, the organization lost face and their brand took a hit.”
Another notable attack in 2021 was the work of a group masquerading as REvil, the notorious ransomware operation that purportedly made more than $100 million from ransom payments by the first half of 2021. The copycat group launched an extortion campaign by sending their targets emails threatening to hold systems hostage and to continue DDoS attacking until their demands were met. Retail and wholesale VoIP providers in the UK were targeted first before attacks followed against VoIP operators in Western Europe and North America.
Unfortunately, the copycat group was successful. “One particular VoIP provider said they filed with the U.S. Securities and Exchange Commission (SEC) for between $9 million and $12 million worth of revenue lost,” Hummel said. “It didn’t just impact them as an organization—every single user of their service could no longer make phone calls.” Aside from subscriber losses, reputation hits and the cost of recovering the services added to the collateral damage.
Not only have these cyberattacks crystallized assault capabilities, but Hummel warned that, across the board, industries can also expect to see more DDoS extortion campaigns and ransomware events. The number of attacks swell each time an event is brought up in the media, Hummel said. “The more times you see success stories in the criminal world, the more criminals you’re going to have trying to adopt that success,” he said.
The Netscout report pointed to industry data that shows the average cost of remediating a ransomware attack more than doubled in the past 12 months. Remediation costs, including business downtime, lost orders and operational costs, grew to $1.85 million in 2021 from an average of $761,106 in 2020. That sets the recovery cost at 10 times the size of the ransom payment on average.
Play Defense
If there’s one goal of the report, then, it is to build awareness about the array of threats going after critical infrastructure and how these attacks can potentially cripple a digital supply chain, said Hummel.
The Colonial Pipeline incident serves as another object lesson. On May 6, 2021, hackers gained entry to the largest fuel pipeline in the U.S. The breach occurred through the company’s business network account. Even though Colonial’s operational systems were not directly affected, the billing system was hit with ransomware, according to Zero Day, and the decision was made to shut down the entire gasoline pipeline for the first time in its 57-year history.
“[The Colonial example illustrates] why you must have proper segmentation and permissions in place,” said Hummel. In that instance, a ransomware attack impacted the entire workforce. Hummel argued that if Colonial had instead isolated different parts of their business and created fallbacks, the need to shut down the entire plant might have been avoided.
While DDoS attacks are ever present and adversaries constantly innovate and develop new attack strategies, said Hummel, it is possible to stop 90% of DDoS attacks from being launched with minimal effort through mitigation efforts, including blocking IP address spoofing and controlling inbound traffic, as well as implementing current best practices and leveraging intelligent DDoS mitigation solutions.
The concluding remarks in the latest Netscout Threat Intelligence Report is a word to the wise: “In many cases, attackers are targeting organizations and service providers that have been lulled into a false sense of security because they aren’t the usual targets. But just because attackers haven’t focused as much attention on a particular vertical in the past in no way signals that they won’t do so in the future.”
Related Videos
Cybercrime Mitigation: Is Your Critical Infrastructure Secure?
Cybersecurity: DDoS Attacks Knock Organizations Offline
Report: DDoS Cyberattacks Pile Pressure on Critical Manufacturing Sector